- within Finance and Banking topic(s)
- with Senior Company Executives, HR and Finance and Tax Executives
- in United States
- with readers working within the Accounting & Consultancy, Advertising & Public Relations and Banking & Credit industries
ASIC has reviewed how Australian financial services advice licensees and their Authorised Representatives (ARs) utilise and engage with offshore service providers along with a second review of Responsible Entities. ASIC's reviews, released in October 2025, focus on licensees' risk management systems, including cybersecurity and privacy frameworks. The recommendations included in ASIC's reviews of are relevant to all Australian Financial Services Licensees, even if they are not giving advice or acting as REs.
ASIC's position is that whilst licensees can outsource certain functions, such as administrative operations, advice support and client communication, the licensee remains responsible for complying with its obligations under the Australian Financial Services Licence (AFSL). ASIC's review highlights ongoing concern that licensees do not have adequate arrangements in place to appoint, assess and monitor offshore outsourced services, particularly by its ARs.
Whilst the review focuses on advice licensees, there are lessons to be learned for all licensees in relation to engaging offshore service providers.
Key Risks associated with the use of Offshore Service Providers:
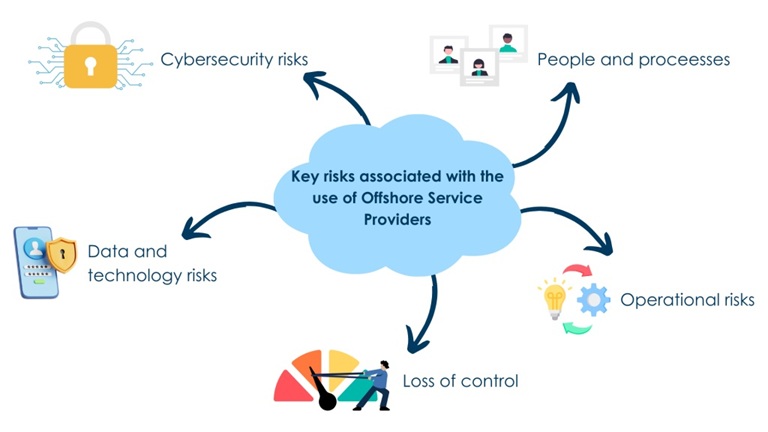
- Loss of Control- licensees may lose control over certain business functions which creates confidentiality and privacy issues.
- Data and Technology risks - licensees may lose access to sensitive client information due to offshore service providers being subject to foreign laws which do not align with Australian laws.
- Cybersecurity risks - licensees may not be able to effectively detect and manage data breaches or cybersecurity incidents due to functions being based offshore.
- Operational risks - offshore infrastructure may be less reliable, causing disruptions to information technology services.
- People and processes - licensees have reduced oversight and governance over people and processes that are based offshore, impacting its ability to effectively carry out its supervisory arrangements.
Key Findings:
ASIC outlined nine (9) key findings which have been summarised in the table below. ASIC have also included some examples of good and poor practices:
| Appointment of Offshore Service Providers | |
|---|---|
Examples of good practices observed:
|
Examples of poor practices observed include failing to have policies and processes in place for ARs to use when engaging with offshore service providers. |
| Offshore Service Providers Disclosure to Clients | |
| Examples of good practices observed include providing statements in disclosure documents such as Financial Services Guides noting that client information may be provided to offshore service providers. | Examples of poor practices observed include failing to disclose to clients the use of offshore service providers and whether express consent is required. |
| Monitoring and Ongoing Compliance | |
Examples of good practices observed include:
|
Examples of poor practices observed include failure to conduct and document audits of outsourced service providers. |
| Approved Outsourced Services Providers | |
Examples of good practices observed include:
|
Examples of poor practices observed include:
|
| Authorised Representatives use of Outsourced Service Providers | |
| Examples of good practices observed include being aware of all outsourced functions used by ARs. | Examples of poor practices observed include failure to identify ARs use of outsourced service providers. |
| Cybersecurity | |
Examples of good practices include:
|
Examples ofpoor practicesinclude:
|
| Privacy and Data | |
Examples of good practices include:
|
Examples of poor practices include the failure to conduct assessments of data security and protections implemented by offshore service providers. |
| Offshore Service Providers access | |
| Examples of good practices include implementing real-time alert tools to detect unauthorised access or suspicious activities. | Examples of poor practices include:
|
| Management of Incidents | |
Examples of good practices include:
|
Examples of poor practices include broad, undefined policies in the event of a security incident or system failure. |
Review of Responsible Entities' use of Offshore Service Providers:
ASIC also reviewed the use of offshore service providers among responsible entities of registered managed investment schemes.
Examples of poor practices included:
- failure to consider jurisdictional risks as part of due diligence processes;
- failure to define level of resourcing required for monitoring offshore service providers;
- no requirements imposed on offshore service providers to comply with responsible entities' existing cyber frameworks;
- failure to assess offshore regulatory environment regarding data security and data protection;
- failure to audit system access or activity logs; and
- data protection arrangements were not triggered by changes in threats, vulnerabilities, cyber incidents or changes to data handling.
Examples of good practices include:
- conducting enhanced due diligence on offshore service providers due to risks associated with jurisdictional, data access, security and privacy;
- having clearly defined metrics to measure service levels;
- maintaining minimum operational and managerial competencies;
- procedures in place to identify, escalate and resolve breaches;
- assessing cyber risks regularly in accordance with industry standards or frameworks;
- having in place documented response strategies for high-risk situations such as cyber-attacks; and
- conducting audits on data handling arrangements regularly.
Key Takeaways
It is important that licensees have effective risk management systems in place for identifying and monitoring the risks of utilising offshore service providers.
Licensees should consider taking the following steps to enhance compliance with its obligations:

- undertaking due diligence when selecting suitable service providers, including approving use by ARs;
- implementing an offshore outsourcing policy;
- monitoring ongoing performance of its offshore service providers, including undertaking independent assessment and verification of cybersecurity measures and handling of client information;
- ensuring adequate risk management systems are in place for assessing and monitoring risks of offshore service providers;
- appropriately dealing with any breaches in accordance with service level agreements;
- regularly reviewing and documenting each AR's compliance with the licensee's outsourcing policies and procedures; and
- setting up real-time alerts for access violations and suspicious activities
Failure to adequately supervise outsourced functions can result in the licensee breaching its general conduct obligations and risk suspension or cancellation of the AFSL.
Background
Licensees have obligations under section 912A(1) of Corporations Act 2001 (Cth), namely, to:
- have adequate risk management systems in place;
- have available adequate resources (including financial, technological and human resources) to provide the financial services covered by the licence; and
- carry out supervisory arrangements.
Further Reading
- Review of offshore outsourcing - Financial Services advice licensees
- Review of offshore outsourcing - Responsible entities
- Regulatory Guide 104 - Meeting the general obligations
- Representatives Policy
- Outsourcing Policy
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

